Skip to content
Welcome to Nihon Communication Solutions Pvt Ltd.
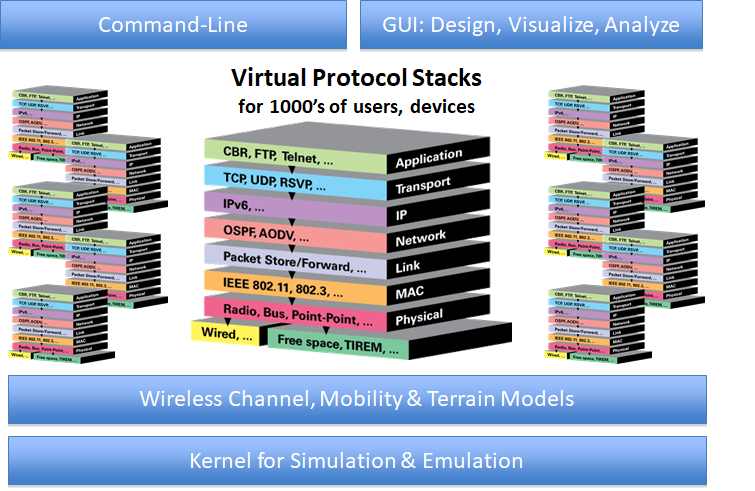
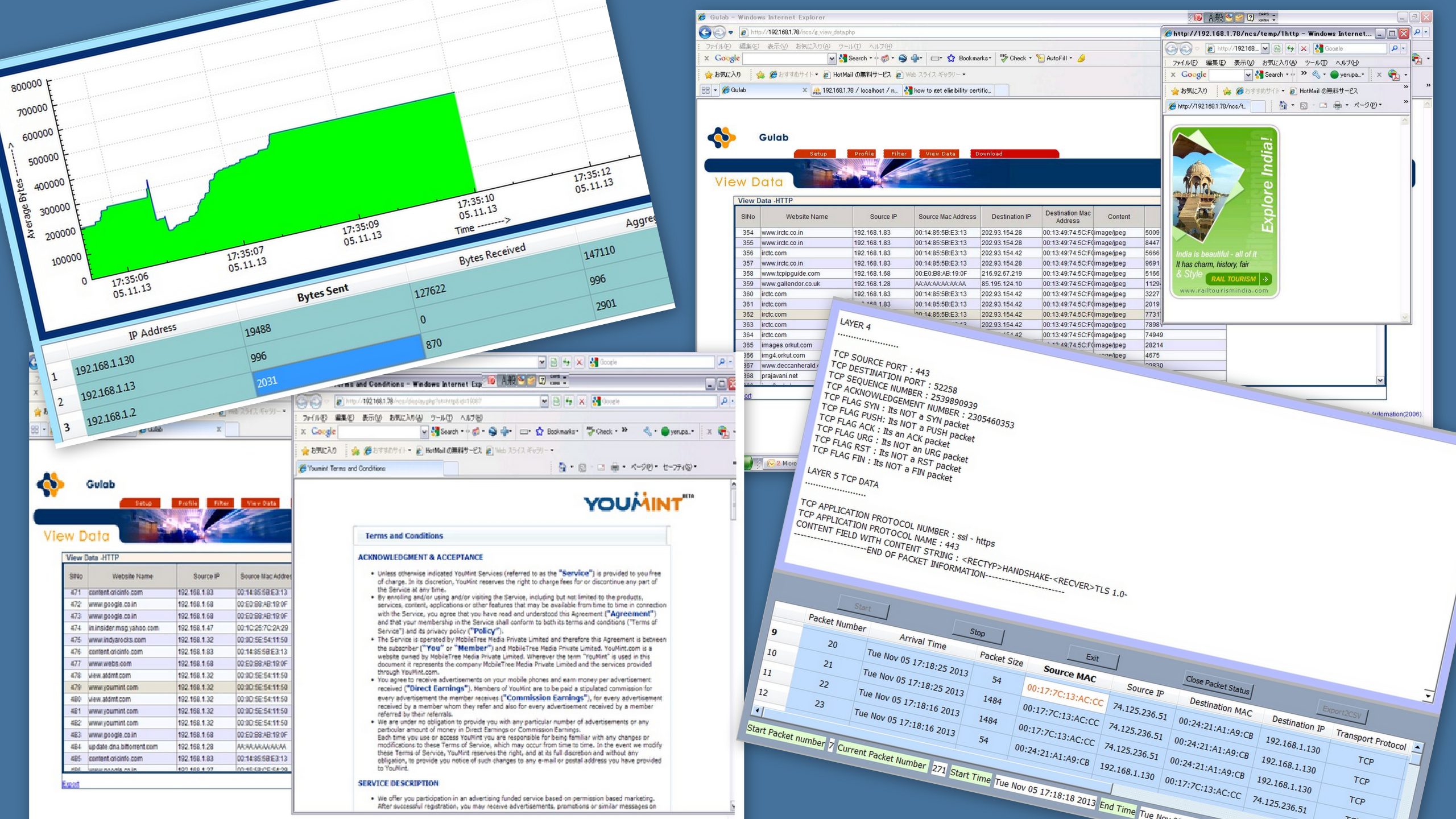
Nihon Communication Solutions Pvt, Ltd (NCS) has a strong focus on providing IT solutions in various areas such as network security, network simulation and emulation for wired and wireless networks, IoT sensor networks, data center solutions, AI and ML solutions, and IP stack development for military radios. As a subsidiary of NIHON OFFICE Co., LTD, Japan, NCS is well-positioned to provide IT solutions for both Indian and Japanese customers.